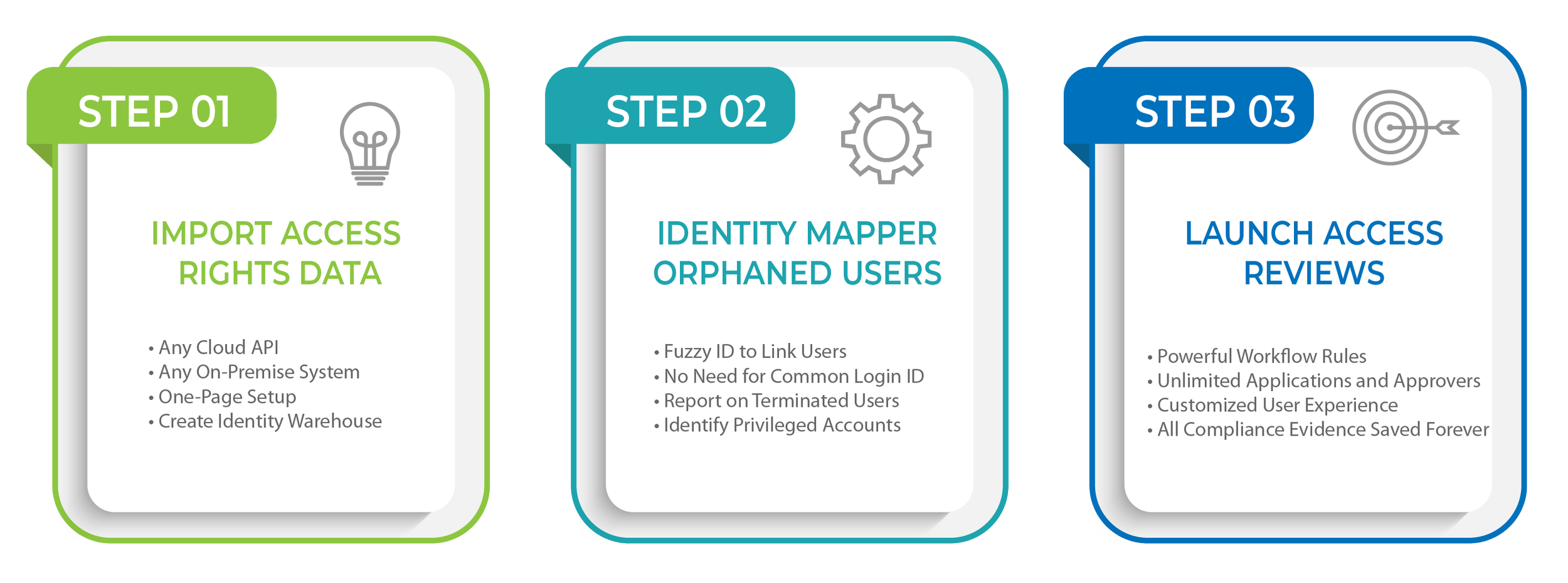
3 Steps to Automate User Access Reviews
User access reviews do not need to be a hard and time-consuming process. With the right automation tools, your entitlement reviews can be fully-automated in a matter of weeks. With Access Auditor, you can automate your reviews in 3 easy steps.1) Import Data From All Applications
The key with data imports is being able to quickly integrate with all types of applications.Cloud API: You need a simple way to configure API connections to anything in the cloud. Access Auditor allows for unlimited connections to any REST API. All setup is configured by your browser with no custom coding or scripting.Active Directory and Databases: Make direct connections to any LDAP or database server.Legacy and Text Exports: Import from any text or excel report.
2) Create Identity Warehouse with the Identity Mapper
The second step is to link users from every application to find accounts that were left behind. We want to build an identity warehouse where we know who has access to what across every application. The challenge for many of us is that we don't always have a unique identifier to reconcile the same person in each application. Some systems might share an SSO ID while others may have a value like email or employee ID. These various keys can be used to link user accounts. But many other systems have no common identifier. In those cases, we turn to the Fuzzy ID. The Fuzzy ID module uses a custom patter matching algorithm to identify users from various systems based upon a name that seems "close". Even if we use nicknames or names are misspelled, the Fuzzy ID can find these matches and let you join them in the identity warehouse with the push of a button.Once we have our identity warehouse created, a simple report shows all of the accounts that are not linked to an active employee, partner, or contractor. We can then address those orphaned accounts promptly to ensure strong identity governance.3) Launch User Access Reviews
With the data imported, starting an access review should be a simple push of a button. We need not only simplicity, but also powerful features like role-based reviews, workflow rules, and customized user page layout.Role-Based Reviews: Using SCC's Role Manager, you can define business roles based upon access rights that are common by title, location, job code, or other parameters. When we start our role-based access reviews, we highlight exceptions to the roles.Workflow Rules: While we often need reviews to be performed by user managers or application owners, we typically have more custom exceptions to that process. We need workflow rules to assign approvers based upon user or privilege data, allowing us to review all applications at once and send approvals to the right person.Customize User Experience: Software tools typically come with a default layout for the review, showing common user and privilege parameters. But most of us are not default and we need to customize the headers of the review, the layout, and the descriptions. Access Auditor gives you full control over what your users see when doing their reviews.Compliance Evidence: All the certifications and completed reviews are saved forever in Access Auditor. But not only are the user responses preserved, but Access Auditor also tracks and validates the inappropriate permissions have been removed. Integration with the Access Manager will automate the removal of access and termination of users.
Summary
With these 3 simple steps, Access Auditor can automate your user access reviews and streamline your entire identity program. To learn more, just reach out to book a demo and we'll learn how quickly we can have you automated.User Access Reviews in 3 Steps
NEXT STEPS
Schedule a demo to learn how you can automate your user access reviews in under one week.