Revolutionizing Identity Governance with User Access Risk Analytics
Executive Summary
In today’s complex enterprise environments, managing user access effectively is paramount for security and compliance. Traditional access review processes often struggle to keep pace with dynamic access changes, leading to overlooked risks and inefficient operations. Security Compliance Corp’s (SCC) Access Intelligence addresses this critical challenge by leveraging advanced machine learning to proactively identify, analyze, and mitigate user access risks. This white paper outlines how Access Intelligence enhances identity governance, providing customizable risk analytics, pinpointing critical vulnerabilities, and transforming user access reviews into a strategic, risk-based exercise.
The Growing Challenge of User Access Management
Modern organizations face an escalating struggle with user access management. As digital footprints expand and regulatory landscapes evolve, ensuring that every user has precisely the right level of access – no more, no less – becomes a monumental task. Enterprises grapple with:
- Exploding Data Volumes: A vast and ever-growing sea of user, role, and entitlement data.
- Dynamic Access Changes: Constant shifts due to new hires, role changes, terminations, and project-based assignments.
- Compliance Demands: Strict regulatory requirements (e.g., SOX, GDPR, HIPAA) necessitating demonstrable control over access.
- Insider Threats & Data Breaches: The critical need to prevent unauthorized access, whether malicious or accidental.
Traditional approaches, often reliant on manual reviews or static rule sets, are inherently reactive and insufficient. They create “blind spots” where inappropriate or risky access can persist undetected, leaving organizations vulnerable to data breaches, compliance failures, and operational inefficiencies.
The Problem: Unseen Risks in Traditional Access Reviews
Many organizations conduct periodic user access reviews to meet compliance obligations. However, these reviews frequently fall short:
- Overwhelming Data: Reviewers are often presented with mountains of data without context or prioritization, leading to “check-box” exercises rather than genuine risk assessment.
- Lack of Insight: Without intelligent analysis, identifying anomalous or high-risk access buried within legitimate entitlements is incredibly difficult and time-consuming.
- Inefficiency: Manual processes consume significant resources, diverting valuable time from security teams that could be spent on more strategic initiatives.
- Reactive Posture: Issues are typically identified after the fact, if at all, rather than proactively flagged for intervention.
This leads to a paradox: while reviews are conducted, the true underlying risks may remain hidden, undermining the very purpose of identity governance.
Introducing Security Compliance Corp’s Access Intelligence
Security Compliance Corp’s Access Intelligence is a sophisticated, AI-powered solution designed to bring clarity, precision, and efficiency to identity governance. By applying machine learning algorithms to an organization’s Identity Warehouse, Access Intelligence proactively identifies and prioritizes user access risks that traditional methods miss. It transforms raw access data into actionable insights, enabling organizations to move from a reactive to a proactive security posture.
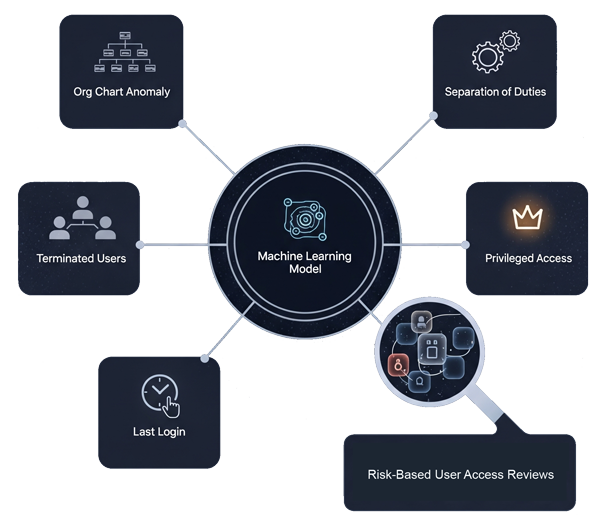
Key Capabilities of Access Intelligence
Access Intelligence is built upon a foundation of intelligent analytics, offering several core capabilities:
1. Customizable Risk Analytics
At the heart of Access Intelligence is a powerful machine learning model that adapts to your unique environment. Unlike rigid, off-the-shelf solutions, SCC’s platform allows for:
- Tailored Risk Criteria: Organizations can define and include various criteria relevant to their specific industry, compliance needs, and risk appetite. This ensures the model identifies risks pertinent to your business.
- Contextual Understanding: The AI learns from your organizational structure, roles, and historical data to identify deviations and anomalies that signal potential risk.
- Dynamic Adaptation: As your environment changes, the machine learning model continuously learns and refines its risk identification capabilities, ensuring ongoing relevance.
2. Precise Identification of Critical Risk Items
Access Intelligence goes beyond generic alerts, providing specific and actionable identification of diverse risk categories:
- Org Chart Anomalies: Pinpoints users whose access rights are inconsistent with their defined role or position within the organizational hierarchy. For example, a marketing specialist with high-level finance system access.
- Terminated Users with Access: Detects accounts belonging to individuals who are no longer employed but still retain active access, a significant security vulnerability.
- Separation of Duties (SoD) Conflicts: Automatically flags instances where a single user holds conflicting access rights that could enable fraud or error (e.g., the ability to both create and approve purchase orders).
- Privileged Access Review: Highlights users with highly privileged or sensitive access entitlements, ensuring these critical accounts receive the closest scrutiny.
- Stale Accounts (Last Login): Identifies inactive accounts based on last login data, helping to manage dormant access that could be exploited.
3. Enhanced Risk-Based User Access Reviews
Access Intelligence revolutionizes the user access review process by embedding risk insights directly into the workflow:
- Prioritized Reviews: Focuses reviewers’ attention on the highest-risk users and access rights, significantly reducing review fatigue and improving efficiency.
- Contextual Information: Provides reviewers with clear, concise insights into why an access right is flagged as risky, empowering them to make informed decisions.
- Exception Management: Facilitates the identification and management of legitimate exceptions to enterprise roles, streamlining the review of non-standard access.
- Targeted Scrutiny: Allows organizations to limit the scope of reviews to only the most sensitive users and access rights, ensuring comprehensive coverage where it matters most.
4. Seamless Integration with Access Auditor
Access Intelligence is not a standalone module; it is deeply integrated into SCC’s Access Auditor identity governance solution. This synergy means:
- Unified Governance: Risk analytics are woven throughout the entire identity governance lifecycle, from provisioning to de-provisioning and continuous monitoring.
- Actionable Reporting: User access risks are presented clearly in risk reports, offering a holistic view of your security posture.
- Direct Workflow Integration: Critical risk insights are directly surfaced within user access reviews in Access Auditor, allowing reviewers to address identified issues immediately within their familiar interface.
The Transformative Benefits of AI-Powered Access Intelligence
By deploying Security Compliance Corp’s Access Intelligence, organizations can achieve significant benefits:
- Enhanced Security Posture: Proactively identifies and remediates hidden access risks, dramatically reducing the attack surface and potential for data breaches.
- Streamlined Compliance: Provides clear, auditable evidence of risk-based access control, simplifying compliance with regulatory mandates.
- Increased Operational Efficiency: Automates the identification of complex risks, saving countless hours for security, compliance, and IT teams.
- Improved Review Accuracy: Empowers reviewers with intelligent insights, leading to more accurate and effective access decisions.
- Optimized Resource Allocation: Directs resources to the most critical areas of risk, ensuring maximum impact from security investments.
Conclusion
In an era where identity is the new perimeter, traditional approaches to access management are no longer sufficient. Security Compliance Corp’s Access Intelligence stands as a beacon of innovation, offering a powerful, AI-driven solution to the complex challenge of user access risk. By delivering customizable analytics, precise risk identification, and seamlessly integrated workflows, Access Intelligence empowers organizations to achieve true identity governance – secure, compliant, and efficient.
Take the Next Step
Discover how Security Compliance Corp’s Access Intelligence can transform your identity governance strategy. Contact us today for a personalized demonstration and learn how to gain unprecedented clarity into your access risks.
