
Customizable Risk Analytics
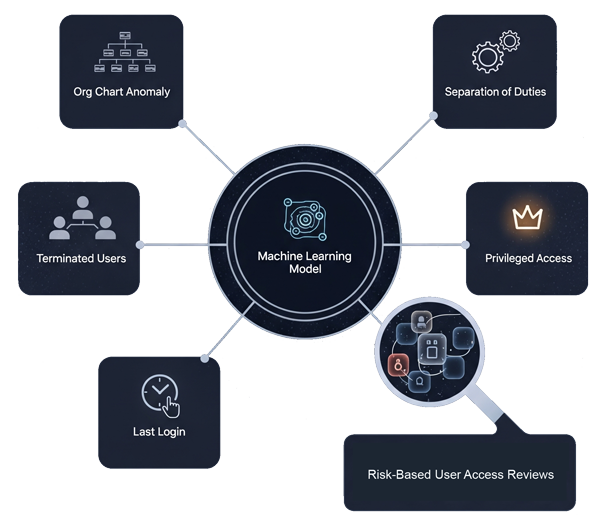
SCC’s Access Intelligence uses a machine learning model to better fit your unique environment. Various criteria can be included to identify user access risks and focus your efforts on the most sensitive users. Some of the risk items include:
- Org Chart Anomaly: Users with access to systems not common for their job.
- Terminated Users: Unknown or terminated users with access generate a red flag.
- Separation of Duties: Configure SOD conflicts to include violations in your risk analysis.
- Privileged Access: Users with highly-privileged access may need to be reviewed more closely.
- Last Login: When users are not actively using applications, the accounts may become stale and should be disabled if not needed.

Risk-Based User Access Reviews
Improve the user access review process with insights gained from Access Intelligence. The risk-based insights will:
- Make reviews more effective by highlighting areas of concern for extra scrutiny
- Highlight exceptions to your enterprise roles
- Limit user access reviews to only the most sensitive users and access rights
What could have been a time-consuming requirement for the entire company is instead a non-event, giving IT high marks for easy-to-use automation.



